How to Run Your Own Breach Audit (Step-by-Step)
🧭 How to Run Your Own Breach Audit
Breach headlines are everywhere. The good news: you can run a personal breach audit in an hour or two and lock things down fast. Below is a clear, step-by-step playbook that ties into our guides on free password managers and open source vs. security through obscurity (why transparency matters for password managers, VPNs, and apps).
🧑⚖️ Before You Start: What “breach” actually means
A breach can dump email addresses, passwords, security questions, even MFA backups into criminal hands. Your job is to limit the blast radius: spot where you reused credentials, rotate secrets, and harden your most important accounts first. PCMag’s breakdown is a great primer on what really happens during a breach and what to do next. :contentReference[oaicite:0]{index=0}
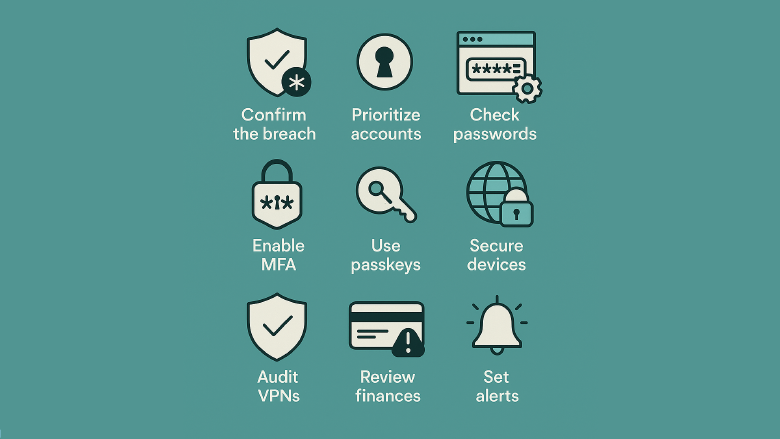
✅ The Breach Audit Checklist (10 steps)
1) Confirm the breach & what data leaked
- Don’t click links in messages claiming there’s a breach; go to the company’s site or trusted news.
- Check if your emails show up in known dumps with Have I Been Pwned (HIBP). Set alerts for future hits. :contentReference[oaicite:1]{index=1}
2) Prioritize the crown jewels
Secure these first:
- Your primary email (often the reset key to everything)
- Your password manager account or vault
- Banking/crypto, work accounts, Apple ID / Google account
This order matches how attackers try to pivot after a breach. :contentReference[oaicite:2]{index=2}
3) Password manager actions (Bitwarden, Proton Pass, KeePass, etc.)
- Change your master password to a long, unique phrase.
- Review breach reports inside your manager and rotate anything flagged.
- Enable 2FA on your manager itself.
- KeePass users: verify your installer came from the official site only — there were recent trojanized KeePass fakes circulating. If you installed from a mirror or “bundle” site, reinstall from the legit source and re-check your machine. :contentReference[oaicite:3]{index=3}
Free choices that still work across devices: Bitwarden and Proton Pass (see our free picks). If you want more features, see our paid guide: Best Password Managers.
4) Rotate reused passwords (start with the risky ones)
Anywhere you reused the same password as a breached site, change it now. Your manager can sort by reused or weak to speed this up. PCMag stresses this as a top action after breaches. :contentReference[oaicite:4]{index=4}
5) Turn on MFA/2FA everywhere that matters
- Prefer app-based 2FA (TOTP) or hardware keys over SMS.
- New: Proton Authenticator is a free, open-source 2FA app for iOS, Android, Windows, macOS, and Linux, with encrypted sync and import from other apps. Good alternative if you’re leaving Google/Microsoft authenticators. :contentReference[oaicite:5]{index=5}
6) Adopt passkeys where available (with one caveat)
Passkeys defeat phishing and password reuse. Use them wherever your manager or platform supports them (Apple, Google, Microsoft, and many major sites). Caveat: passkeys aren’t easy to export/migrate between ecosystems yet, though industry work is underway on standardized import/export. Plan as if you may be tied to your current provider for a while. :contentReference[oaicite:6]{index=6}
7) Secure your devices (Windows, macOS, Linux, Android, iOS)
- Update OS & browsers first.
- Remove shady extensions and old apps.
- Run a trusted AV scan if you installed from sketchy sources (especially after that trojanized-KeePass wave).
These basics shut down a huge chunk of real-world attacks. :contentReference[oaicite:7]{index=7}
8) Review your VPN & app footprint
- If you used a closed-source VPN or app that asks for broad permissions, consider switching to vendors with open code and independent audits (e.g., Mullvad/Proton VPN clients are open-source). Transparency helps catch problems faster — secrecy alone isn’t protection. (See our open-source vs. obscurity guide.)
9) Monitor & lock down financial identity
- Turn on bank/credit alerts; if payment data was exposed, freeze credit where supported.
- Watch for SIM-swap vectors: add a carrier PIN and remove your phone number as a primary recovery method where possible. PCMag and AP News both recommend these moves. :contentReference[oaicite:8]{index=8}
10) Set up ongoing early-warning
- Keep HIBP notifications on.
- In your password manager, keep breach monitoring enabled if available.
- Calendar a 30-minute quarterly audit to catch drift. :contentReference[oaicite:9]{index=9}
🧩 Notes for specific setups
KeePass (Windows/Mac/Linux/Android/iOS via ports)
- It’s offline by default; if you sync via cloud, store your database and key file separately and enable vault merge to handle edits from multiple devices. Verify downloads come from the official project. :contentReference[oaicite:10]{index=10}
Bitwarden / Proton Pass
- Both support breach reports, password health, and TOTP 2FA storage; change the master password, enable 2FA on the account, and rotate anything flagged compromised. (See our free/paid guides for feature details.)
Android & iOS
- Audit app permissions and turn off background access you don’t need.
- Prefer browser autofill from your manager over random “helper” apps.
Operating systems
- Keep automatic updates on. If you ever installed tools from unofficial mirrors (torrents, “bundle” sites), consider a clean reinstall for peace of mind — especially after installing security tools.
🔐 Why we push MFA and passkeys
- MFA (2FA) adds a second factor the attacker usually doesn’t have. With Proton’s new cross-platform, open-source Authenticator, there’s little reason not to enable it. :contentReference[oaicite:11]{index=11}
- Passkeys stop phishing and password reuse outright — they’re the future. Just remember the migration/export story is still evolving; a FIDO import/export standard is in draft, but broad, seamless portability isn’t universal yet. :contentReference[oaicite:12]{index=12}
🧠 Quick FAQ
Do I need to change every password after a breach?
No. Prioritize: email, password manager, finance, shopping sites with saved cards, and any reused passwords. Then chip away at the rest. :contentReference[oaicite:13]{index=13}
Should I ditch password managers because they’re “a single point of failure”?
No — they reduce risk by eliminating reuse and spotting breaches. Just protect the vault with a strong master password and MFA, and use reputable/open providers. :contentReference[oaicite:14]{index=14}
Are passkeys ready for everyone?
They’re great where supported and nearly phishing-proof. But switching providers later can be clunky until standardized export/import lands everywhere. :contentReference[oaicite:15]{index=15}
What if I installed a password manager from a third-party site?
Reinstall from the official source and run a malware scan. The trojanized-KeePass incident shows why provenance matters. :contentReference[oaicite:16]{index=16}
🧩 Keep going
- See our Best Free Password Managers
- Compare premium features in Best Password Managers
- Learn why open source beats secrecy-only approaches in security-critical tools (password managers, VPNs, mobile apps)
Stay calm, do the steps, and set alerts. Breaches happen — but they don’t have to happen to you twice.
