Email Threat Awareness in 2025: Phishing, Quishing, and AI-Driven Scams
🛑 Email Threat Awareness in 2025: What You’re Up Against
While spam filters and security software catch millions of malicious emails every day, attackers in 2025 are more creative, more automated, and more convincing than ever. Understanding the threats is your first line of defense in keeping your email secure.
🚨 Modern Threats You’ll Actually See in 2025
1. AI-Generated Spear-Phishing
Criminals now use AI tools to craft flawless, personalized emails that mimic your writing style or the tone of trusted colleagues. These messages:
- Reference recent meetings, social media posts, or projects.
- Arrive at times when you’re likely distracted (e.g., Friday afternoons).
- Include links or attachments tailored to your job role.
Example: An email “from your boss” referencing a document you really did work on last week, complete with matching tone and company branding — but the link leads to a credential-harvesting page.
For extra protection against compromised credentials, monitor your accounts using Have I Been Pwned or a trusted password manager.
2. Deepfake Voicemail & Callback Phishing
Some attacks start outside the inbox:
- You get a voicemail or email saying there’s an “urgent payment issue” with your bank account.
- The voice in the recording is an AI deepfake of your bank’s customer service agent.
- The callback number routes to the attacker, who collects your login or security codes.
This technique sidesteps the email body entirely — making it harder for filters to detect.
In these cases, strong multi-factor authentication and independent verification are critical.
3. QR Code Phishing (“Quishing”)
Attackers embed malicious URLs inside QR codes sent via:
- Email attachments
- Inline images
- PDFs disguised as tickets, invoices, or event invites
Because spam filters often struggle to scan QR codes inside images, these slip through security layers more easily.
🛡 How Attackers Bypass Spam Filters
Even with advanced AI scanning, spam filters aren’t perfect. Here’s how criminals dodge them:
- Image-Based Payloads: Embedding malicious links in images or PDFs instead of plain text.
- Domain Lookalikes: Using Unicode characters to create deceptive URLs (e.g.,
paypaI.comwith a capital “i” instead of “l”). - Time-Delayed Payloads: Sending clean links that later redirect to malicious sites after initial scanning.
- Reply Chain Hijacking: Breaking into one account, replying to an existing conversation, and slipping in malware or fake invoice links.
This is why human judgment is still crucial — filters can’t catch everything. See our Inbox Organisation Tips for ways to make suspicious messages easier to spot.
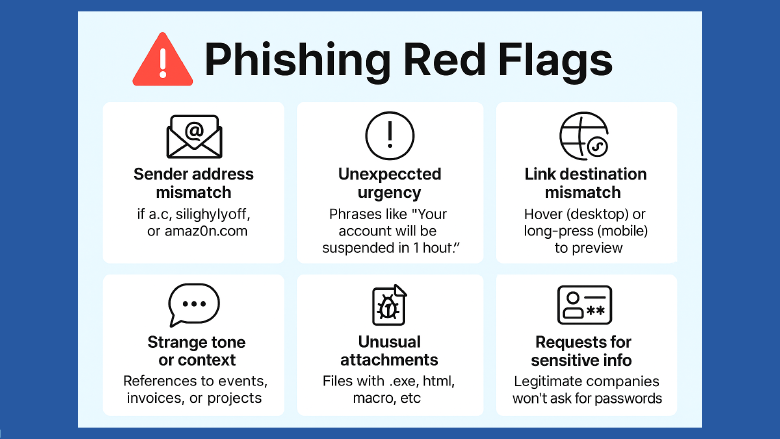
📋 Phishing Red Flags Checklist
| ✅ Check | What to Look For |
|---|---|
| Sender address mismatch | Name looks right, but domain is slightly off (e.g., amaz0n.com or .co instead of .com). |
| Unexpected urgency | Phrases like “Your account will be suspended in 1 hour!” designed to rush decisions. |
| Strange tone or context | References to events, invoices, or projects you’ve never heard of. |
| Link destination mismatch | Hover (desktop) or long-press (mobile) to preview — domain should match the real site exactly. |
| Unusual attachments | Files with .exe, .html, or unexpected macros in Word/Excel documents. |
| Requests for sensitive info | Legitimate companies don’t ask for passwords or codes via email. |
💡 Pro Tip
Treat every unexpected message as suspicious until proven safe — even if it appears to come from someone you know.
If it involves money, login credentials, or urgent action, verify through a second channel (phone call, in-person, or a known official site) before clicking or replying.
For ongoing safety, pair threat awareness with email security best practices, passkeys where possible, and privacy tools like a VPN or one from our best free VPNs list.
