Self-Hosting for Security: Take Back Control of Your Data in 2025
🏠 Self-Hosting for Security: Take Back Control of Your Data in 2025
Most online services—email, password managers, VPNs—run on someone else’s servers. That means your sensitive data sits in a company’s data center, subject to their policies, their security measures, and, in some cases, government demands.
Self-hosting flips that model: you run the services yourself, on hardware you control. It’s not for everyone—it requires some technical know-how—but the trade-off is maximum privacy, customisation, and resilience.
🖥️ The Building Blocks of a Self-Hosted Setup
Before you dive into services, you’ll need the right foundation.
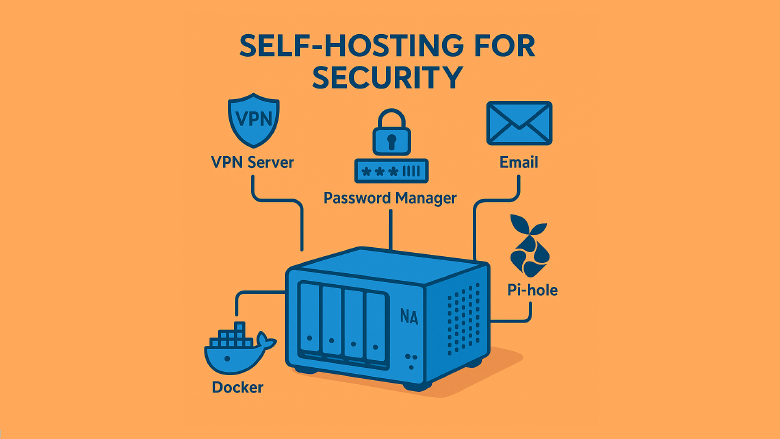
1. A NAS (Network Attached Storage)
A NAS is like your own personal cloud. Popular options:
- Synology – Easy UI, supports Docker
- QNAP – Powerful, flexible, but more complex
- DIY – Build with a mini PC or server
Your NAS becomes the central hub for storage, backups, and container hosting.
2. Docker
Docker makes it simple to run multiple services on the same machine in isolated “containers.”
- Easy to deploy new apps
- Simple updates via image pulls
- Rollback options if something breaks
🔐 Self-Hosting Essential Security Tools
1. Password Manager
Self-hosted password managers like Vaultwarden (a lightweight Bitwarden server) let you:
- Store credentials locally or on your NAS
- Sync securely across devices
- Avoid relying on a third-party cloud
Tip: Pair with strong multi-factor authentication to secure the admin interface. For more options, see our best password managers and best free password managers.
2. Email
Hosting your own email gives you total control over mailboxes, filtering, and storage.
- Tools: Mailcow, Mail-in-a-Box, Poste.io
- Pros: Privacy, custom domains, no scanning by third parties
- Cons: Spam filtering and deliverability can be challenging without proper setup
If you want more control, see our guide to keeping your email secure.
3. Pi-hole
A self-hosted DNS sinkhole that blocks ads and trackers across your network.
- Runs on a NAS, Raspberry Pi, or even a Docker container
- Cuts down on tracking at the network level
- Speeds up browsing by blocking unwanted domains
4. VPN Server
Run your own VPN to:
- Encrypt all traffic leaving your home network
- Secure connections while traveling
- Access your home network remotely
Popular options: WireGuard (fast and modern), OpenVPN (widely supported)
Bonus: Combine with a VPN client on your NAS to route only certain apps through a commercial provider — see our best VPNs and best crypto VPNs if privacy is a priority.
📦 Why Docker Changes the Game
Before Docker, self-hosting multiple services meant configuring them manually—dependencies, updates, backups, all handled by hand. With Docker:
- Every service is portable
- No “dependency hell”
- One-click redeploys
Docker Compose lets you manage entire stacks (e.g., Vaultwarden + database + reverse proxy) in a single file.
⚖️ Self-Hosting: Pros and Cons
Advantages:
- Full data control
- Customisable to your needs
- No ongoing subscription fees (beyond hardware and power)
Challenges:
- Higher setup time and maintenance
- Security is your responsibility
- Hardware failure = downtime (unless you have redundancy)
🚀 Getting Started Safely
- Start small – Try Pi-hole or Vaultwarden first.
- Use backups – Store them offline and offsite.
- Enable MFA – Protect every admin panel.
- Keep software updated – Outdated apps are prime targets.
- Monitor logs – Watch for unusual activity.
📌 Final Word
Self-hosting is the ultimate expression of digital independence. It’s not as plug-and-play as paying for a cloud subscription, but if you value privacy, security, and control, it’s worth the effort.
And the best part? You don’t have to go all-in at once. Start with a password manager or Pi-hole, then expand to email and VPN as you get more comfortable. Every service you bring in-house is one less that’s exposed to third-party risk.
